Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole and optionally a DHCP server, intended for use on a private network.
Pi-Hole can become an all around DNS Solution. Pi-hole includes a caching and forwarding DNS Server. After Pi-Hole applies its blocking lists, it forwards requests made by clients to the upstream DNS servers like Cloudflare, Google or others. This leads to privacy concerns because you can never be sure that the upstream DNS service is not logging where you are going.
In the worst situation, a DNS upstream provider can be compromised by attackers which could poison DNS entries. This can potentially affect millions of users at once. Instead of going to your bank’s IP address, you could be sent to an identical looking phishing site hosted on some off-shore island. This has happened.
If you operate your own tiny recursive DNS server, then the likeliness of getting affected by such an attack becomes extremely small.
Recursive DNS servers resolve their queries by consulting the servers authoritative for a given query by traversing the domain.
We can bypass upstream servers by setting up the node that the pi-hole is already running on as a recursive DNS server. On behalf of a client on your network, the recursive DNS server will traverse the path of the domain across the internet to deliver the proper answer for a query without an upstream DNS provider like Google, Cloudflare or your ISP’s DNS.
We can can configure the Pi-hole server as your own recursive DNS server. This means that the recursive DNS server will have the capability to send a query to the DNS Root servers on the internet. For example, it could look up xyz.net by sending a query to the top level domain (TLD) DNS server for .net. The TLD server answers with the server who has the authoritative answer for xyz.net. The recursive server will answer the Pi-hole with the correct address, which will relay that to the client. The Pi-hole will cache all these lookups for access in the future.
Unbound is a secure open-source recursive DNS server that does exactly this. To install it, log into the console port of your Pi-hole:
sudo apt install unbound
We now need a configuration file:
wget -qO- https://www.internic.net/domain/named.root | sudo tee /var/lib/unbound/root.hints
Now, we want to configure unbound to:
-
Listen only for queries form the local Pi-Hole installation (on port 5335)
-
Listen for both UDP and TCP requests
-
Verify DNSSEC signatures, discarding bogus domains
-
Apply security settings.
sudo nano /etc/unbound/unbound.conf.d/pi-hole.conf
In the editor, paste the following:
server:
# If no logfile is specified, syslog is used
logfile: "/var/log/unbound/unbound.log"
verbosity: 3
interface: 127.0.0.1
port: 5335
do-ip4: yes
do-udp: yes
do-tcp: yes
# May be set to yes if you have IPv6 connectivity
do-ip6: yes
# You want to leave this to no unless you have *native* IPv6. With 6to4 and
# Terredo tunnels your web browser should favor IPv4 for the same reasons
prefer-ip6: no
# Use this only when you downloaded the list of primary root servers!
# If you use the default dns-root-data package, unbound will find it automatically
#root-hints: "/var/lib/unbound/root.hints"
# Trust glue only if it is within the server's authority
harden-glue: yes
# Require DNSSEC data for trust-anchored zones, if such data is absent, the zone becomes BOGUS
harden-dnssec-stripped: yes
# Don't use Capitalization randomization as it known to cause DNSSEC issues sometimes
# see https://discourse.pi-hole.net/t/unbound-stubby-or-dnscrypt-proxy/9378 for further details
use-caps-for-id: no
# Reduce EDNS reassembly buffer size.
# Suggested by the unbound man page to reduce fragmentation reassembly problems
edns-buffer-size: 1472
# Perform prefetching of close to expired message cache entries
# This only applies to domains that have been frequently queried
prefetch: yes
# One thread should be sufficient, can be increased on beefy machines. In reality for most users running on small networks or on a single machine, it should be unnecessary to seek performance enhancement by increasing num-threads above 1.
num-threads: 1
# Ensure kernel buffer is large enough to not lose messages in traffic spikes
so-rcvbuf: 1m
# Ensure privacy of local IP ranges
private-address: 192.168.0.0/16
private-address: 169.254.0.0/16
private-address: 172.16.0.0/12
private-address: 10.0.0.0/8
private-address: fd00::/8
private-address: fe80::/10
Save the file.
create the log file.
sudo mkdir -p /var/log/unbound
sudo touch /var/log/unbound/unbound.log
sudo chown unbound /var/log/unbound/unbound.log
sudo service unbound restart
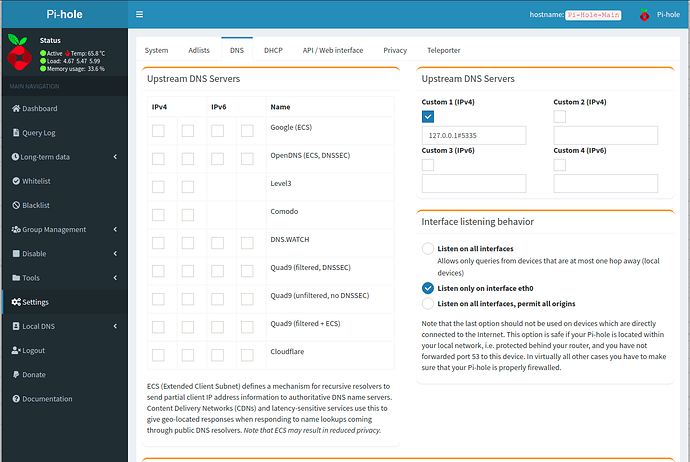
Now go to the Pi-hole admin screen and choose settings and DNS. disable all upstream servers and make your upstream server 127.0.0.1#5535 as in the screenshot.