Years ago it used to be that the only place that you found passwords might be on a personal computer login, if at all. Currently, we are overwhelmed daily with massive numbers of usernames and passwords for our applications.
The biggest reason for so many passwords is that there has been a migration from applications located on the desktop computer to web-based applications in the cloud. Everyone has usernames/passwords for their bank, credit card sites, Amazon, cell phone company, electric company, gas company, internet service providers and the list goes on an on.
Most people create passwords that they can remember or they write them down in a book that they keep some place.
How long will it take to crack your password?
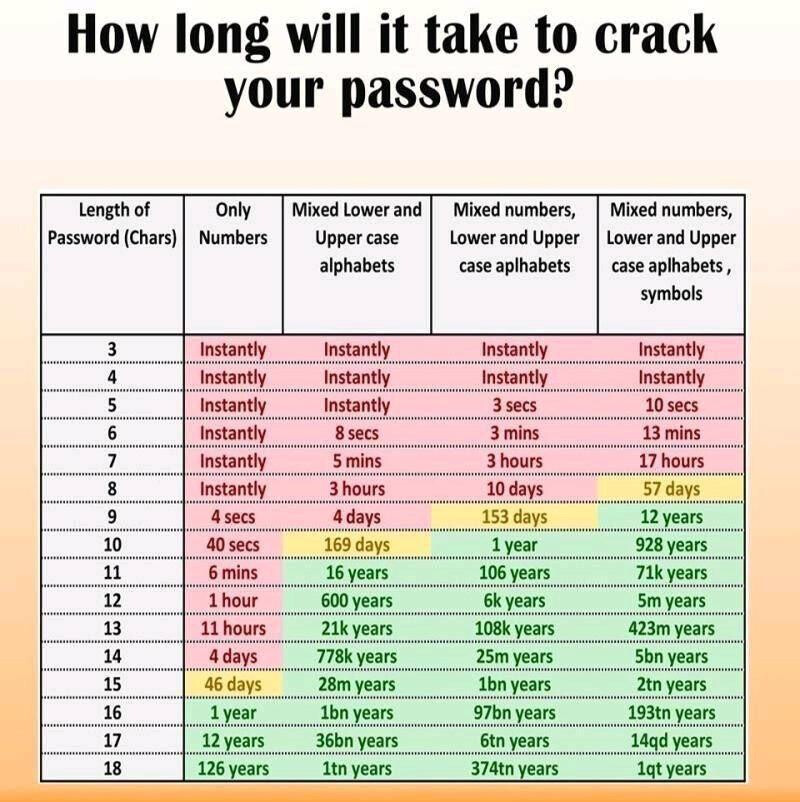
One way to make your password more secure is to add two factor authentication (2FA) to the account that you are accessing. Two factor authentication means something you have and something that you know in order to log in.
The something you know is your username and your password. The something that you have is usually something like a USB Yubico key or a Time-based One time password (TOTP). The Yubico key is a USB thumb drive that you insert into your computer as a part of the login process after entering your username and password. The TOTP key is most commonly either an SMS text message or a Google Authenicator key.
I believe that you should always enable 2FA anywhere that you can. An SMS TOTP is better than no 2FA, but SMS is inherently insecure and hopefully SMS will be replaced with Rich Commnication Services (RCS) which provides end to end encryption unlike SMS. RCS may be on the horizon in coming years.
That being said, Google Authenticator makes for a reasonable 2FA key provider. However, the problem with authenticator is that it has to exist on ONE of your devices which is normally your phone and until recently was difficult to migrate to a new device.
For that reason, I recommend a password manager. Password managers can track usernames, passwords, and even 2FA keys for all of your websites. Password managers are not all created equal. Some password managers are available only on some platforms and only allow you to sync passwords to a few devices and some password managers do not manage 2FA keys.
To be highly effective, you need a password manager that can run on all the common web browsers and also has an application for Windows, Mac, IOS, Android, and Linux. There are several popular password managers out there and Nordpass, LastPass, McAfee True Key, and 1Password are examples.
I personally prefer Bitwarden. Bitwarden is OpenSource and also potentially self-hosted which means that you can run it on your own server or on a cloud instance like AWS. Bitwarden can host as many users as required. Each Bitwarden user has a “Vault”. A vault is a collection of all of the usernames, passwords and 2FA keys for all the sites that you access. Bitwarden also supports the storing of credit cards, drivers licenses, passport info, and even private notes.
Your password vault can even be “exported” to a file and imported to any other Bitwarden server. When you use Bitwarden, you are using a client based version of the program or a web add-in. The program makes updates and additions to your Bitwarden server anytime that you add or change a password or web site logon information.
If you are unable to reach your Bitwarden server for any reason, you can still use the client on any of your devices to authenticate to a website. You can also use the browser add-in to authenticate to any web site even if your Bitwarden server is not reachable. When your Bitwarden server is reachable, any changes or updates are then transferred to the server and synced to all your Bitwarden clients.
So, even if your Bitwarden server is unreachable, all of your information has a locally cached copy and you can still log into any sites that you have Bitwarden manage your passwords for. Bitwarden, unlike other password managers does not limit the number of clients that you can sync your data to.
If you install the web browser add-in, Bitwarden will ask you if you want to save information for any new website that you are signing into.
Bitwarden also supports secure end to end encrypted sending of notes. You can put the information you want to send in a “Send” and then provide the URL to the recipient. All data including “Sends”, Usernames, Passwords, and 2FA keys are stored encrypted on the Bitwarden server.
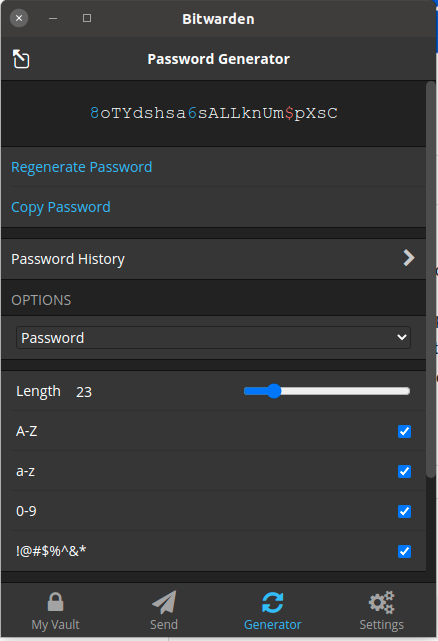
Bitwarden also has a built-in password generator to create passwords to use on your various websites. You can select the complexity and length also.
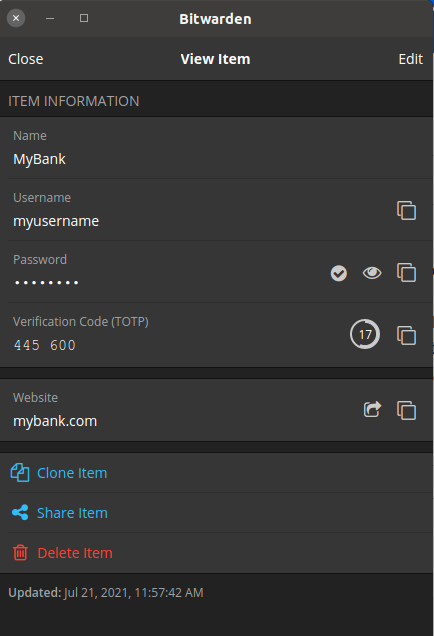
Here is an example of an entry in Bitwarden. I added a fictitous sitte at https://mybank.com and a username, password, and 2FA TOTP key.
The main screen for Bitwarden lists items like Logins to websites, credit cards, Identity (drivers license), and secure notes. You can have as many as you want of each and be assured that they are encrypted via AES-CBBC 256 bit encryption.
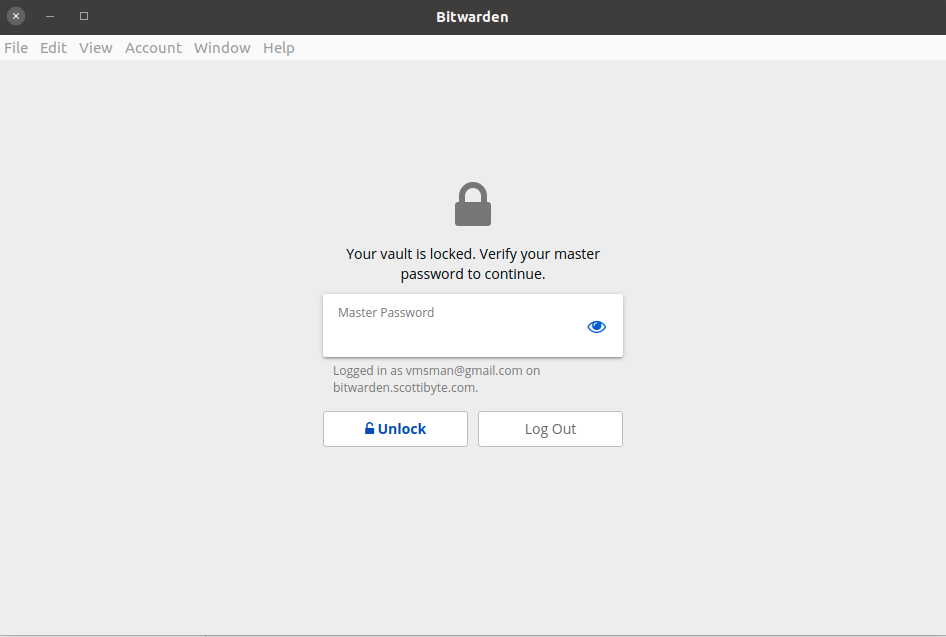
When you launch the bitwarden app or you access the bitwarden web broawser add-in, you are prompted for your master password.
Bitwarden has a premium membership that costs $10 a year. The premium features include the 2FA options, the TOTP authenticator, encrypted file attachments, and emergency access. The 2FA options also support Duo, Tubikey, and FIDO hardware key authentication. The premium license is per user and not per server. It is possible to host as many users as you like on a server.
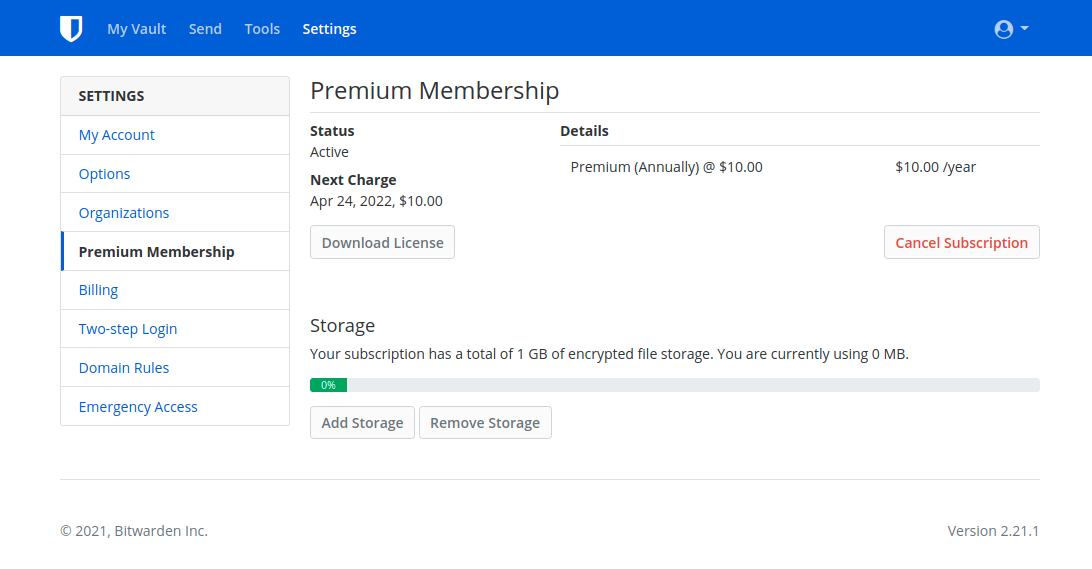
Bitwarden itself is free and open source. The premium license cost of $10 a year adds great features and is well worth it to help with their development costs.
It’s easy to host Bitwarden on any server instance, even on a Raspberry Pi. I think the advantage to self-hosting Bitwarden is that you are in control of your own server and your own encrypted data. The only caveat to self-hosting is that you need a domain name for full functionality from outside your network.